🍻In-Depth Rootbeer SDK Bypass (Native) pt 1
Simple and easy Rootbeer SDK study and bypass
I Love the Rootbeer SDK, not only because of the name (it's a fucking awesome name) but because it helped me a lot in the start when i was learning about hooking and how to use frida effectively.
If you don't know, Rootbeer is a kit of protections aiming at android applications that have the need of detecting whenever the device is rooted.
As a open source protection it's easier for us pentesters to read their code and study how their protections work, to, when you find this SDK at a pentest you already know where to hook to bypass this one completely.
There's a lot of ways to bypass that SDK when you encounter this at a pentest. Some of them are easy and boring and some of them are BADASS.
Some easy and boring way would require you to decompile, modify the return values and recompile the application, maybe some hooks that involves returning false to every function of the SDK. Yeah, we are not going to do that. As this techniques could not be used in future pentests, we will make a native/generic bypass to every check of the Rootbeer SDK. YAY Overcomplicating simple things hahaha
In-Depth of Every detection of rootbeer SDK
This will be divided in two parts, just because I'm trying to get the other detections of rootbeer to work haha
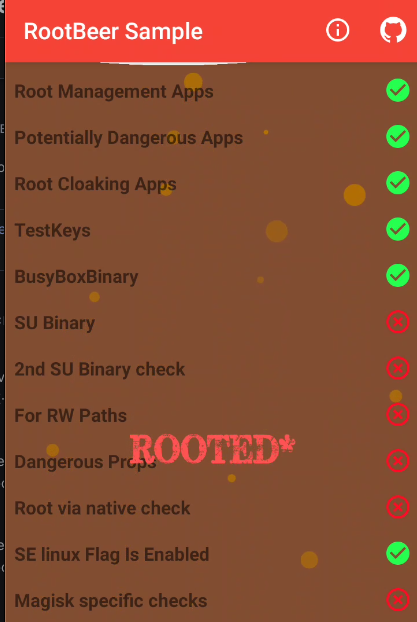
We will begin with the ones that are already being detected at my phone:
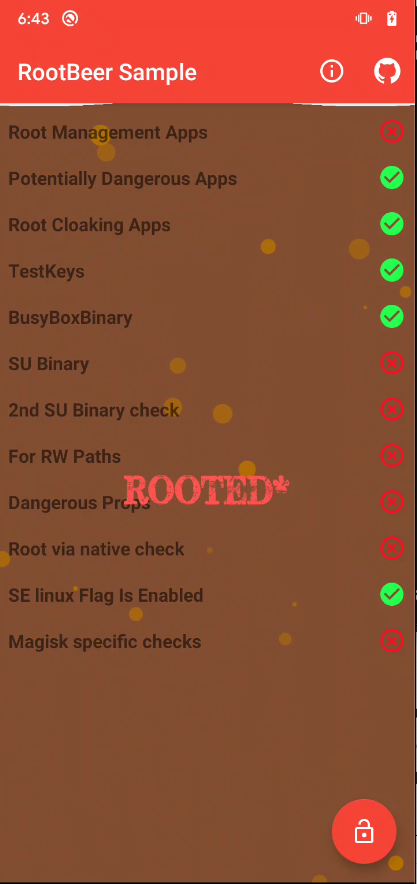
Well we got a lot of work to do in the app... the first protection is the root management apps, so, let's begin
Root Management Apps
First things first, let's understand what this protection does.
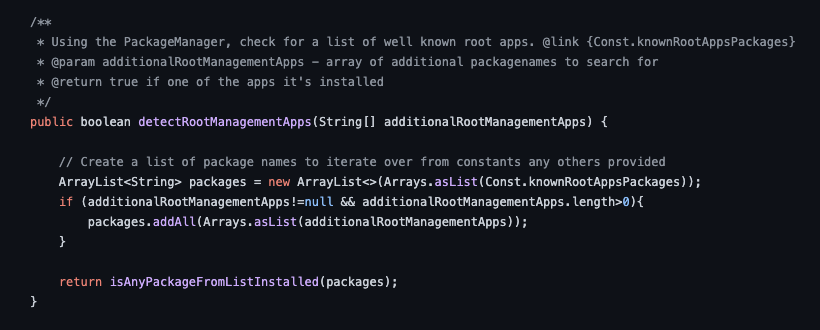
well it basically parses a const and calls another function hahah, let's take a look at this Const that is being passed as list to another function:
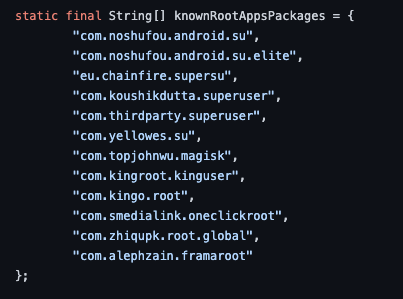
Well, there they are, nothing new here. lets see the other function it's calling:
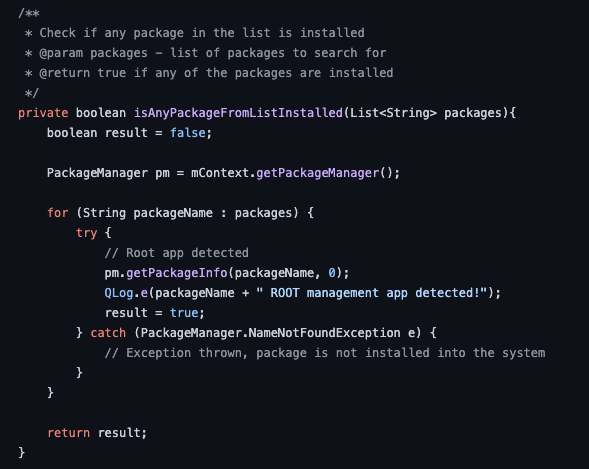
Thats interesting... it`s using the for detecting if any of the packages that we got on consts are present in the device. for bypassing this natively we need to study this java function...
This link shows a bit about this method, and as a native android method we can hook this thing to the ground but first, we need to know what we will do with this function.
Well, if you think a bit about this function it receives a package name and some flags that we could not care less...
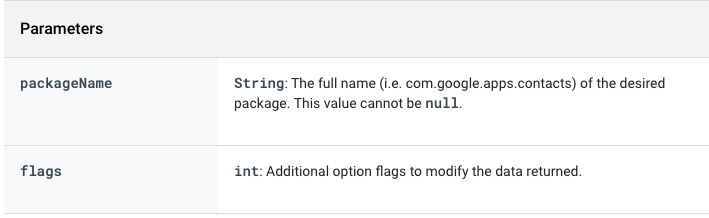
so package name... one option is to modify the package name to anything that does not exist, so that we can bypass this... other option is to return something that will benefit us. in this case is to throw an exception...
Any of this are feasible... as we like to overcomplicate things we will make a generic-device-specific bypass, if that makes any sense...
To do that we will frida-trace this function to see which of those root packages are present at my device
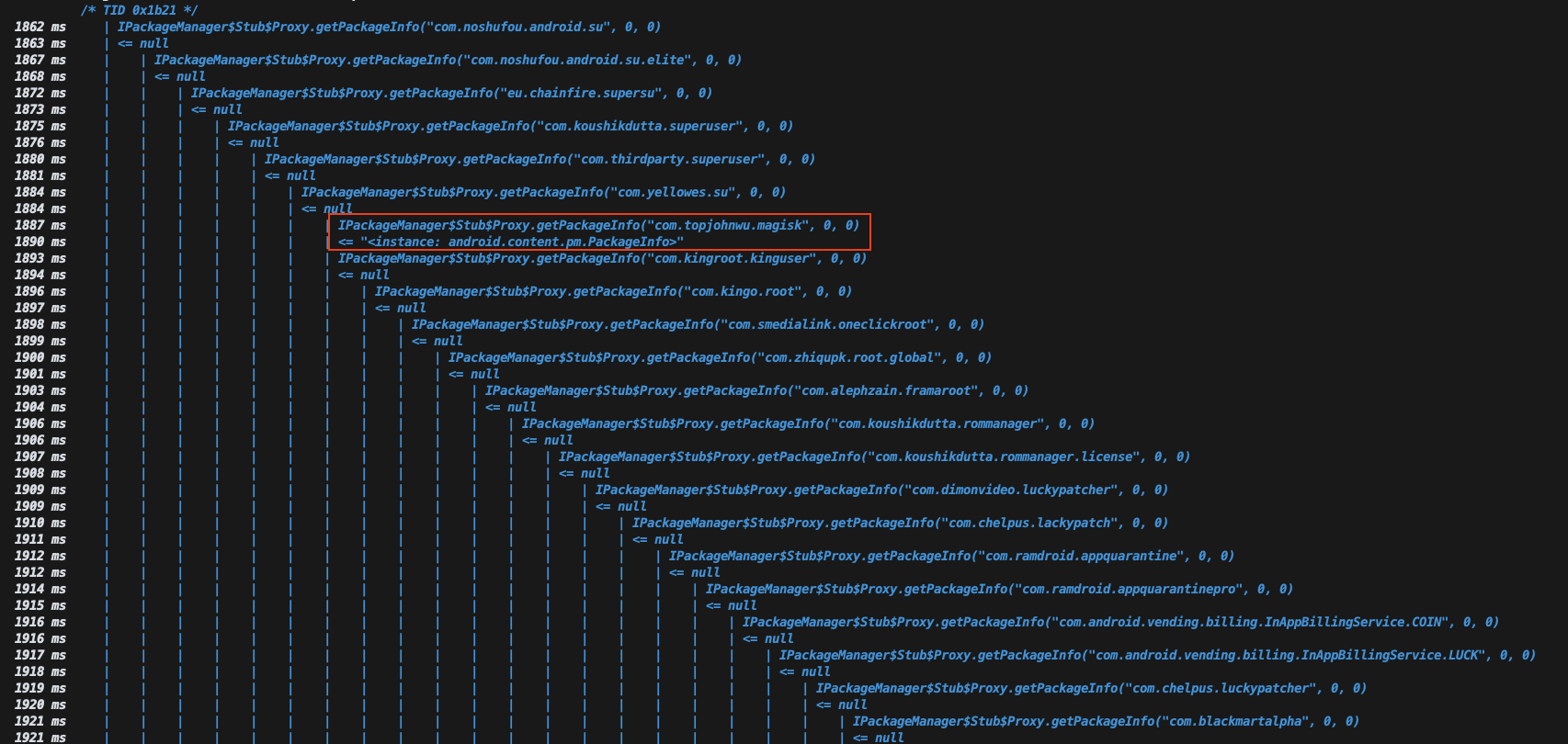
To get this kind of output (with the returns) we need to modify the hooking script that frida-trace creates at __handlers__ . So we found what is fucking us up... so we can do a simple frida script to bypass this one right?
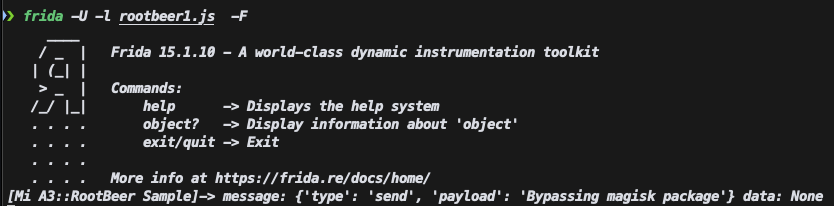
yeah, we got it sniped haha, modified the pkgname to a fake one. and got our first check ! (YAY, i guess)
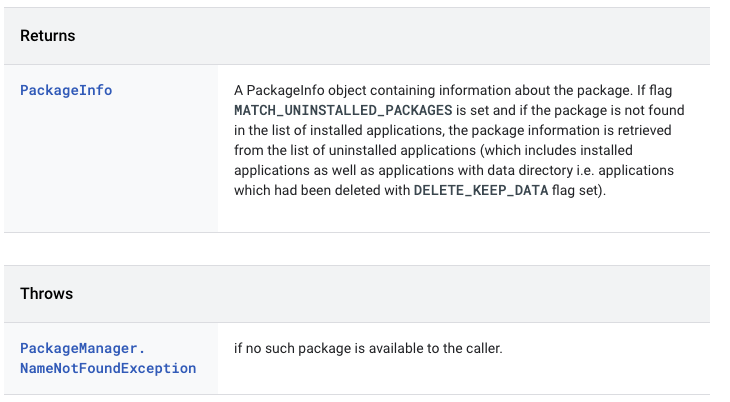
well , the other way is to force a exception, we can see the code of the function we are forcing the exception too, if you are curious.
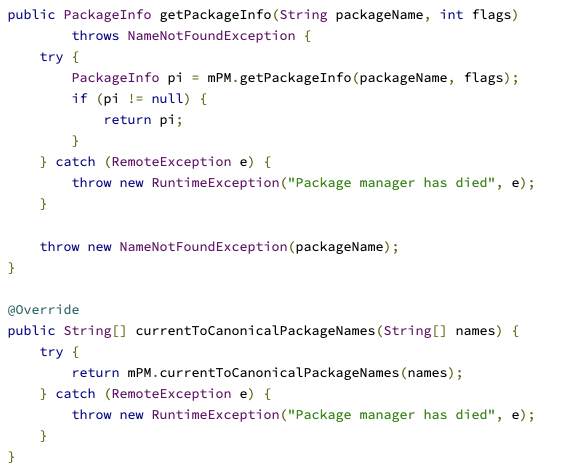
If you force the NameNotFound exception you will get the same result as the exploit said above.
We will exploit SU Binary and 2nd SU Binary check in part 2 :)
