🍃Flutter SSL Pinning Bypass, the hard way
We will get a in-depth view of how it works and how to bypass the SSL Pinning implementation on libflutter.so.

So, Flutter.
Flutter is a SDK created by Google, to develop Android & IOS applications (and a bunch of other stuff). And if you came across a mobile application made with flutter you surely found out a bunch of things that make your life harder as a pentester.
Before we dive deep into the SSL Pinning shenanigans we need to deal with another protection adopted by default on flutter, the proxy bypass
Bypass of the Proxy bypass
You could make a lot of stuff to bypass this protection but all of them needs to force the requests to pass to your proxy, and we will do it with Iptables/pfctl (mac user here, but same rules applies to iptables)
But first we need to make a separate controlled network for us to control. The easiest way i found to achieve this goal was to create a hotspot with my Mac using the sharing tool.
At this point you should connect a Ethernet cable and share this connection using the right network adapter on the sharing tool, making sure that you are sharing your connection though wi-fi.
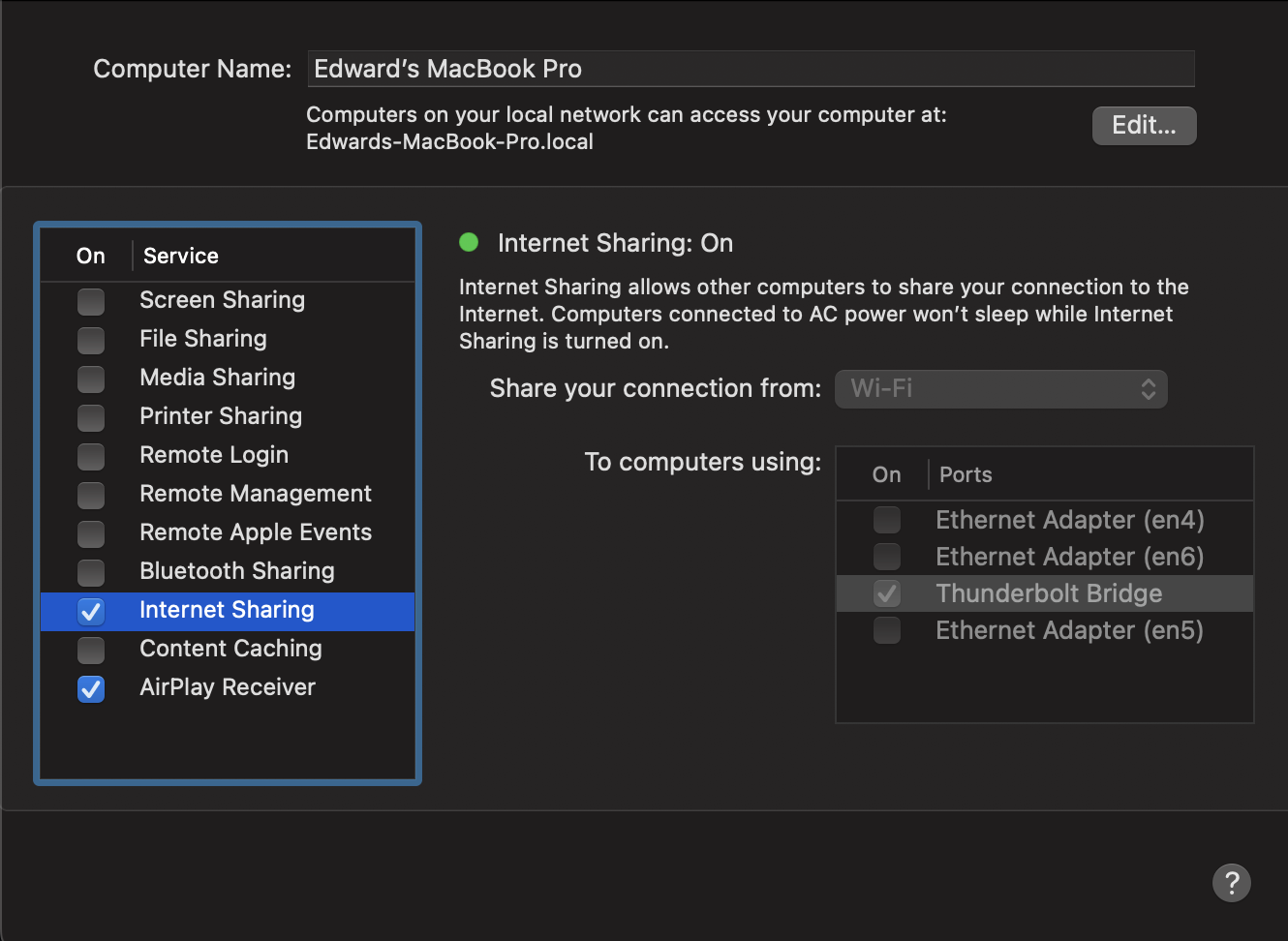
So, it's time for us to create the Iptables/pfctl rules, making sure that every connection of the application is passing through the rules that we create.
As it bypasses the proxy configuration on the device we will set the following rule
I found it useful to add 8443,8000 as some applications that I've tested used 8443 and 8000 to send requests to the API, feel free to enter more ports if you found some at reverse engineering process.
Now we need our device to connect to the wi-fi network that we've setup on the mac